Top 3 Cybersecurity Uses of Reverse WHOIS Lookups
2020.04.23
The WHOIS records of Internet domain names are fonts of information, especially for cybersecurity specialists. And to deal with an ever-growing and -changing threat landscape, cybersecurity teams need all the help they can get. Aid can take the form of tools, application programming interfaces (APIs), or databases. The most important thing is that these products or sources provide reliable and up-to-date information.
An example of this would be a reverse WHOIS API or a reverse domain lookup tool. What a reverse WHOIS query does is to look for domain names that satisfy a search criterion by scanning a comprehensive database of WHOIS records. So instead of looking up the WHOIS records of a domain name, you look up the domain names associated with a particular WHOIS record detail.
Doing so can be relevant to cybersecurity specialists in three main ways.
1. Phishing and Malware Prevention
Around 78% of data breaches and malware infections start with a phishing attack, making it the primary entry point for cybercriminals. There’s also no room for complacency, as 76% of organizations succumb to phishing attacks. Pretty much anyone can become a victim and therefore should be careful.
How can a reverse domain lookup tool help to investigate phishing clues, then? You can start with an email address, a phone number, a company name, or any search term that matches a particular detail found in a WHOIS record. Say, for example, that you notice suspicious emails coming from ghxstspam@yandex[.]com.
In this case, a reverse domain lookup tool would find one domain name that has the email address in its WHOIS record—security-and-safety-action-115204[.]com. A quick check on a threat intelligence platform would tell you that this domain is a known malware host. It is, in fact, listed on PhishTank. As such, blocking access to and from the domain name and email address is probably necessary.
In other instances, cybercriminals can use the same email address to register several domain names. When reverse WHOIS lookups return multiple domains, you can decide whether blocking all of them is the right way to go in order to stay safe from threats.
2. Cybercrime Investigation
In the previous section, we hypothetically helped to prevent a phishing attack from happening with the help of a reverse domain lookup. But what if the cybercrime has already occurred? You can still use the tool the same way so you can start tracing who the culprit behind the threat is.
With the help of a reverse WHOIS lookup tool, you can find out domains that are possibly involved in the same malicious activities. The email address dr[.]talzak@shrespects[.]com, for instance, has been involved in various phishing campaigns that use the COVID-19 pandemic as a lure. When you do a reverse WHOIS search using the email address, you would find 65 domains that use it:
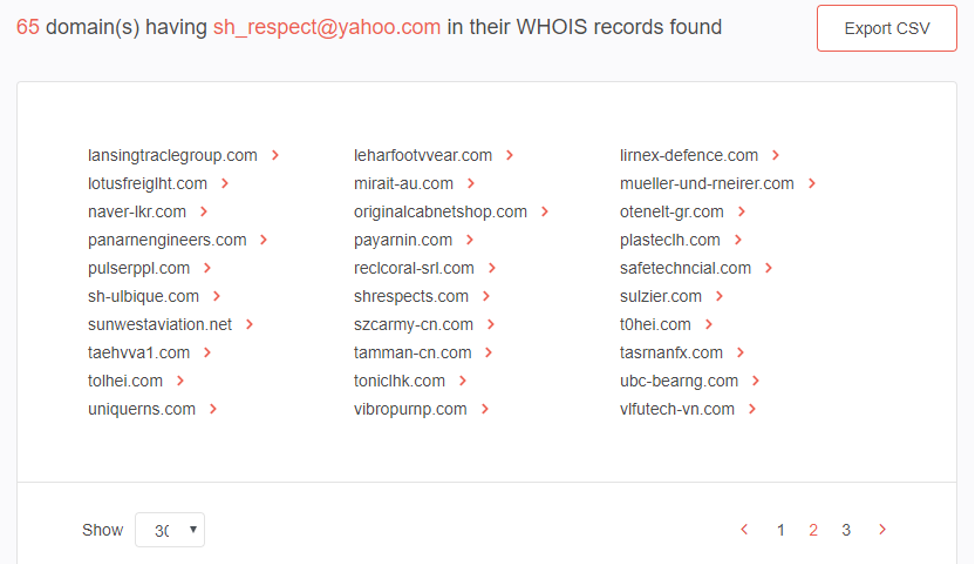
Among the domains is shrespects[.]com, which is a confirmed malware host. Armed with this data, you can build WHOIS reports for each domain to see who owns them and if there are any relationships besides the email address.
Most of the associated domains in our example, including shrespects[.]com, have the following details:
● Registrant Name: SH Respect
● Registrant Street1: 1 Queens BroadWay Osodo
● Registrant City: Lagos
● Registrant State/Province: Lagos
● Registrant Postal Code: 11105
● Registrant Country: NIGERIA
● Registrant Email: sh_respect@yahoo[.]com
● Registrant Phone: 2347089794909
As such, it would be safer to assume that the domains that have extreme similarity with the IoC’s registrant details are owned by the same threat actor. These details would give cybercrime investigators an edge.
3. Brand Protection
Brand protection has ceased to be the sole responsibility of an organization’s legal department. As businesses often predominantly operate online, brand protection should encompass Internet domain names too. One way to protect your brand is to stay on the lookout for potential copycats. These people may be using your company’s name for their gain, or worse, cybercriminals may use your brand in phishing attacks.
Make it a habit to run your brand or company name on Reverse WHOIS Search so you can see how others are using it. Cybersquatters may be taking advantage of your organization by maintaining domains that don’t belong to you but use your brand name.
---
As threat actors continue to come up with more sophisticated infiltration methods, cybersecurity experts must also rally for new and radical tools that can protect their organizations. Reverse domain lookup tools, for one, can aid in preventing phishing and malware attacks, cybercrime investigations, and brand protection. By finding all of the domains related to an email address, a phone number, or a company name, cybersecurity teams can obtain valuable information to work with.
About the Author

Jonathan Zhang is the founder and CEO of Threat Intelligence Platform (TIP)—a data, tool, and API provider that specializes in automated threat detection, security analysis, and threat intelligence solutions for Fortune 1000 and cybersecurity companies. TIP is part of the WhoisXML API family, a trusted intelligence vendor by over 50,000 clients.
More Articles
Copyright © Fooyoh.com All rights reserved.