Ryuk - The Ransomeware that Targets Those Who Have a lot to Lose
2020.06.19
From Death Note to Ransom Note, Ryuk has made it to the digital world. It is now the name of a targeted, well-planned ransomware that has attacked several organizations around the world. Ryuk has targeted various enterprises, encrypting hundreds of storage/data centers and PCs in the infected company while asking for a ransom in return.
The Ryuk ransomware is definitely a problem, but we don’t advise you get tempted to dive right into solving the problem. To avoid it, you should understand what the issue is first. So, here’s everything you need to know about Ryuk.
How Does Ryuk Work?
The world already knows what the ransomware Hermes was capable of. Now, a modified version of that was created in the form of Ryuk.
They both have similar characteristics, but there are some differences. Ryuk identifies and encrypts network devices, storing “deleting shadow companies” on the endpoints.
As for encryption, a second RSA public key is used by Ryuk. As we mentioned, Ryuk focuses on large organizations and government agencies. The bigger the company is, the higher the ransom becomes.
Now, how does the ransomware end up in a system? It starts with phishing emails, sketchy websites, or random pop ups. Direct access is also given through bots such as Emotet and TrickVot. Once in, these two types of bots start spreading laterally through the network and deploy Ryuk ransomware in the process.
There’s some delay between the spreading of the Bots and the deployment of Ryuk, but that’s not a flaw in the ransomware. In fact, it needs this delay so that the Bots can steal private information in order to make organizations vulnerable before Ryuk attacks.
When a suitable system is detected, the following files get uploaded within a subfolder inside the directory:
● PUBLIC: RSA Public Key
● UNIQUE_ID_DO_NOT_REMOVE: Hardcoded Key
Next, Ryuk is fully in and it starts the encryption process using WNetOpenEnum and WNetEnumResource. Now that the encryption is in place, Ryuk sends the following Ransom Notes to the infected target.
● The first Note is a bit more detailed than the second one, stating everything about the demands of the attackers and advising the target not to use third-party decryptors.
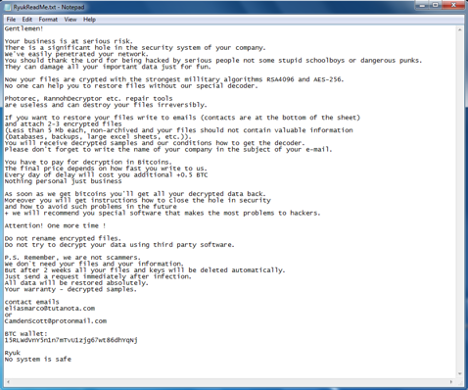
● The second one is a shorter, let detailed note. The attacker cuts to the chase and inform the target that they’re system has been penetrated.
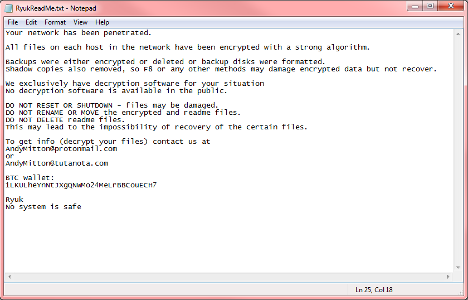
How is Payment Made?
Once the device is infected and the data encrypted, the attackers demand payment via cryptocurrency. To be specific, using Bitcoin. However, before the ransomware asks for the fee, some calculations are made.
Observing the transactions known to Ryuk BTC address, it’s quite obvious how the ransom is calculated. It varies significantly with each attack.
Apparently, WIZARD SPIDER ((like INDRIK SPIDER with BitPaymer) calculates the ransom (fee) amount based on how big and valuable the targeted organization is. The range of ransom varies from 15 BTC to 50 BTC and it has already netted the attackers over $640,000.
When the target receives the ransom note, Ryuk directs it to deposit the fee in a specific Bitcoin wallet. Also, the attackers use highly secure email options, including the likes of ProtonMail and Tutanota.
Final Words
As stated above, Ryuk is not like the ransomware we’re all accustomed to. It is delivered as a payload of the Emotet and Trickbot malware. Even the Tampa Bay Times fell victim to the ransomware attack a while ago. It’s crucial to watch out while browsing the web and never click on shady ads or visit non-secure websites.
While browsing the web, we found a lot of websites, such as The VPN Guru, that provide tips and advice on how to maintain your security and privacy. They’re very good if you want to avoid getting hit with a cyber attack.
More Articles
Copyright © Fooyoh.com All rights reserved.