Identifying Potential Cyber Threats with WHOIS History
2020.11.26
WHOIS history refers to the set of records that reveals a domain name’s ownership changes over time. Looking up the historical WHOIS records of the domain name yahoo[.]com on https://whois-history.whoisxmlapi.com, for instance, revealed that its WHOIS record had undergone 1,554 changes since the tool started tracking its modifications in 2012.
Around 97% of those records are publicly available, including the domain’s change in ownership from registrant Yahoo, Inc! to Oath Inc (formerly AOL). To recall, Verizon-owned AOL acquired Yahoo in 2017.
The ability to look into historical domain name ownership records makes WHOIS history tools handy in threat detection. Among the WHOIS data points the tool provides are:
● Registrant/Administrative/Technical contact name
● Registrant/Administrative/Technical contact organization
● Registrant/Administrative/Technical contact email address
● Registrant/Administrative/Technical contact phone number
● WHOIS server
● Nameservers
● Registrar
In this post, we discussed a few types of domain threats that WHOIS history can help expose.
Phishing and Malware Domains
Phishing is among the top methods cybercriminals use, with almost 147,000 phishing attacks reported in the first half of 2020 alone. The reason behind this is apparent—phishing remains effective.
As such, security teams vigilantly look out for phishing domain names, and WHOIS history can help.
To illustrate, consider the domain name justinstalledpanel[.]com. Historical WHOIS records show that the domain had undergone 440 record changes over 1,642 days of tracking. The registrant organization is ISPsystem LLC.
When security teams search for domain names with the same organization name in their historical WHOIS records, 96 domains would turn up. Tools like Reverse WHOIS API can help simplify the process.
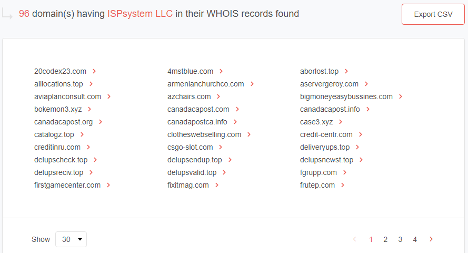
One of domains is canadacapost[.]info, which can be interpreted as potentially suspicious since it looks similar to canadapost[.]ca, the primary postal service company in Canada. As such, it could figure in phishing attacks against Canadian citizens and those that use the postal service. The same is true for canadacapost[.]com and canadapostca[.]info.
By digging up the WHOIS history records of verified phishing domain justinstalledpanel[.]com, security teams get a list of connected domains that could also, at least theoretically, figure in phishing attacks.
Domains Associated with Cybercriminals
A domain name’s past associations can significantly affect its reputability. In most cases, those that have figured in criminal activities are likely blacklisted. But how about domains that are included in a cybercriminal’s arsenal? A WHOIS history tool can help detect them, enabling organizations to avoid accessing potentially dangerous domains.
We cite mezzo[.]cc as an example. An email from this domain or a third-party vendor using mezzo[.]cc should be treated suspiciously. Its WHOIS history record shows that it was owned by Konstantin Volchkov in April 2017. This name is among five people that are wanted by the Federal Bureau of Investigation (FBI) for their involvement in a hacking campaign using the GozNym malware. The group targeted businesses and financial organizations.
Other domains that have the same registrant contact name in their WHOIS history records are const[.]pw and radostdetyam[.]com. While there are no reports that the domains have figured in malicious attacks, their possible association with a convicted felon could be a cause for concern.
---
While it’s true that most threat actors use pseudonyms and privacy protection services, some public records could tie them to potentially suspicious and malicious domain names anyway. Third-party risk assessment, threat detection, and other cybersecurity practices can be made more robust when historical WHOIS data is taken into account.
More Articles
Copyright © Fooyoh.com All rights reserved.